
How to protect Linux operating systems against network scanning ?
You could use Uncomplicated Firewall (UFW) program for managing a netfilter firewall. It provides a command line interface and aims to be uncomplicated and easy to use.
For illustration purpose, we will scan a virtual test machine without firewall enabled and then apply a security measure to limit the surface area attack.
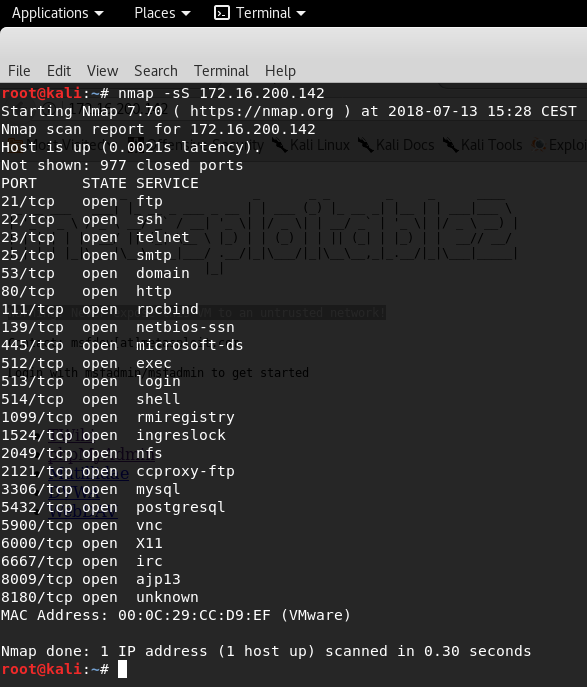
Let’s create a stealth SYN scan with NMAP and see the result.
23 ports are opened
The best practices are uninstall unnecessary programs and services, shudown all ports and allow necessary ports.
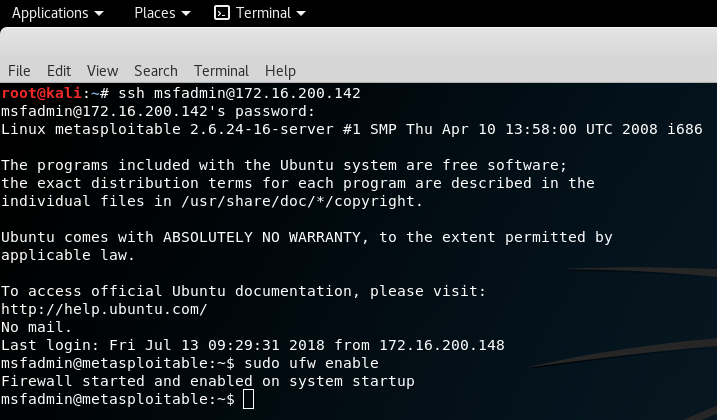
You could close all ports with Uncomplicated Firewall (UFW) program and restart the scanner to verify that all ports are protected.
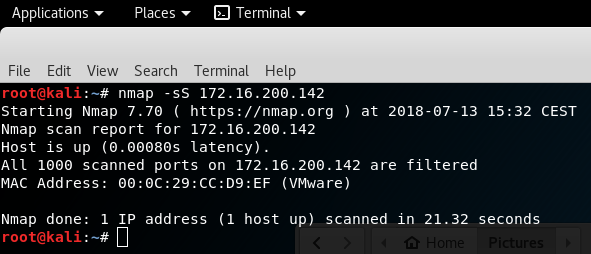
As you could see, all ports are filtered by the firewall and no ports are open. It’s the best policy but with Linux servers, you may need to access remotely via SSH, and in this context, we need to add a rule.
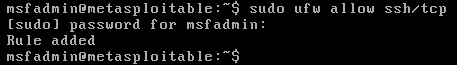
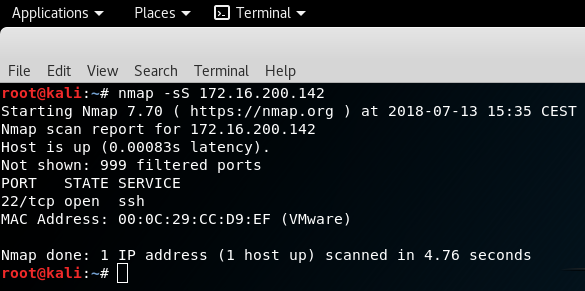
Once the rule is added, we could restart NMAP to verify that SSH port is opened and now you are confident that you will be able to connect to the remote server with the firewall activated.
Your Linux operating system is protected against network scanning because you have reduced the surface area attack. Be sure that all of your opened networks services are up to date to mitigate its vulnerabilities, for more informations, you could refer to this article “Identify Network Vulnerabilities / Nessus“.
Leave a Reply